
Security Bite: North Korean hackers impersonate job recruiters to target Mac users with updated BeaverTail malware
-
by Anoop Singh
- 15

9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
Security researchers have identified an attempt by state-sponsored hackers from North Korea (DPRK) to target Mac users with infostealer malware through a trojanized meeting app.
Once infected, the malware would establish a connection between the Mac and the attacker’s command and control (C2) server to exfiltrate sensitive data like iCloud Keychain credentials. It was also found to quietly install the remote desktop application AnyDesk and keylogging software in the background to take over machines and collect keystrokes.
The malware, a new variant of a known strain dubbed “BeaverTail,” was first reported by MalwareHunterTeam via a post on X. While BeaverTail was an existing JavaScript info stealer discovered in 2023, it now appears to have been reworked to target Mac users with a malicious disk image titled “MicroTalk.dmg.”
Security researcher and author Patrick Wardle analyzed the malware in a fairly comprehensive and hilariously titled blog post on Objective-See. Wardle found that hackers were most likely posing as job recruiters, tricking victims into downloading what appeared to be the legitimate video conferencing platform MiroTalk, hints the “MicroTalk.dmg” disk image file name, but was actually a clone containing hidden malware.
About Security Bite: Security Bite is a weekly security-focused column on 9to5Mac. Every week,Arin Waichulis delivers insights on data privacy, uncovers vulnerabilities, and sheds light on emerging threats within Apple’s vast ecosystem of over 2 billion active devices.

This wouldn’t be the first report of North Korean hackers posed as job recruiters to target victims. Palo Alto Network’s infamous Unit42 research group recently reported on a similar story titled: “Hacking Employers and Seeking Employment: Two Job-Related Campaigns Bear Hallmarks of North Korean Threat Actors.”
According to Wardle’s analysis, the malicous MicroTalk clone containing the malware is unsigned or hasn’t been registered with Apple by an identified developer, so macOS Gatekeeper will prevent the application from executing. However, users can circumvent the block by right-clicking and hitting “Open” from the shortcut menu.

Gatekeeper is a regular headache for cybercriminals targeting Mac users. In fact, it’s become such an effective nuisance that in some cases, they instruct the user to open the malicious application the “Correct” way (aka right-clicking and hitting “Open”) instead of double-clicking.
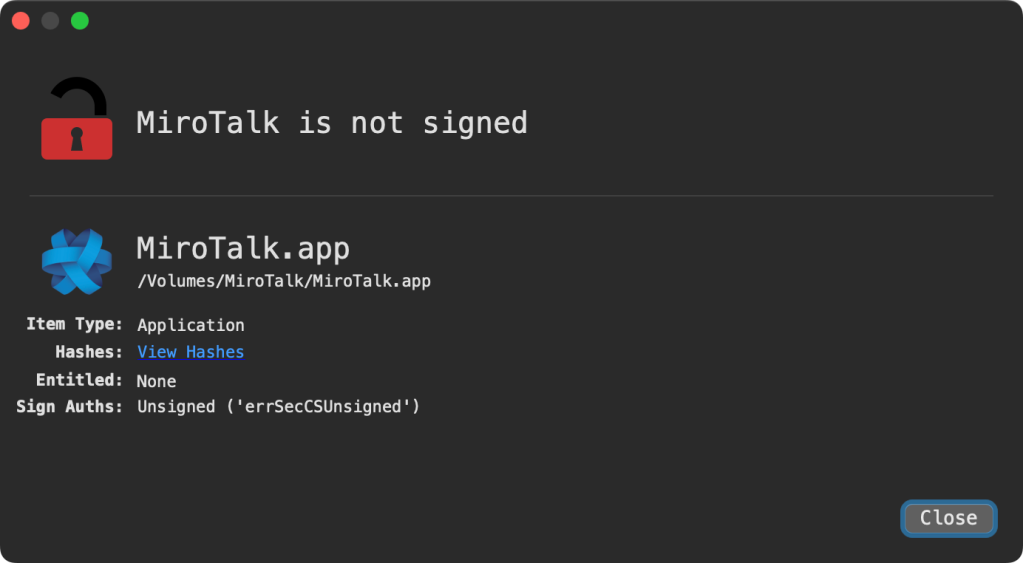
Once infected, the malware communicates with C2 servers to download and extract data, including iCould KeyChain credentials and browser extension IDs of popular cryptocurrency wallets, which can be used to steal private keys and mnemonic phrases. What’s most elusive, however, is when the malware was discovered last week, it could pass through antivirus scanners, like VirusTotal, completely undetected. Cybercriminals will upload their executables on platforms like VirusTotal to ensure the malicious aspects are hidden well enough to remain undetected from popular scanners. The downside is the “good guys” can see them too.
“Specifically from the symbol’s output, we see methods names (fileUpload, pDownFinished, run) that reveal likely exfiltration and download & execute capabilities,” according to Ojective-See’s blog post.
“And from embedded strings we see both the address of the likely command & control server, 95.164.17.24:1224 and also hints as to the type of information the malware collect for exfiltration. Specifically browser extension IDs of popular crypto-currency wallets, paths to user browsers’ data, and the macOS keychain. Other strings are related to the download and execution of additional payloads which appear to malicious python scripts.”
At the end of the day, I wouldn’t be surprised if this is the work of BlueNoroff, a subgroup of the nation-state’s well-known cybercrime enterprise, Lazarus Group. There have been several distinctive cases of BlueNoroff often reaching out to potential victims under the disguise of an investor or company head hunter. If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is a duck.
FTC: We use income earning auto affiliate links. More.

9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the…
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the…
