
5 Best Encryption Key Management Software (Updated for 2024)
-
by Anoop Singh
- 7
Using SSH and encrypting your data are the biggest steps organizations can take to ensure that all their private information remains safe and secure and away from prying eyes. However, there are challenges with managing encryption.
First, losing encryption keys means losing access to data. Second, if a malicious actor gets hold of an organization’s keys, data becomes vulnerable and subject to cyber threats like hacking and ransomware –- no matter how strong the encryption.
SEE: Brute Force and Dictionary Attacks: A Guide for IT Leaders (TechRepublic Premium)
Fortunately, there are a number of tools available that provide encryption key management, keeping keys both secure and easily accessible.
Here are five of the most popular, reliable, and effective encryption key management tools and their features so you can decide which one best fits your needs.
ESET PROTECT Advanced
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Any Company Size
Any Company Size
Features
Advanced Threat Defense, Full Disk Encryption , Modern Endpoint Protection, Server Security
ManageEngine Log360
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Micro (0-49 Employees), Small (50-249 Employees), Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Micro, Small, Medium, Large, Enterprise
Features
Activity Dashboard, Advanced Threat Analytics, Analytics/Reporting, and more
Graylog
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Medium, Large, Enterprise
Features
Anomaly Detection, Audit Logs, Compliance Reporting, and more
Best encryption key management software compared
| Software | Highlight security features | Deployment experience | Free plan or free trial | Starting price |
|---|---|---|---|---|
| Microsoft Azure Key Vault: Best overall | FIPS 140-2 Level 2 hardware security module encryption | Initial setup can be tricky | Free trial | Flat rate of $0.03 per 10,000 operations. |
| GnuPG: Best for PGP encryption | PGP encryption, auditing and compliance capabilities | Easy to use, especially for command line users | Free | Free |
| Seahorse: Best for a user-friendly interface | Auto-saving passwords to a keyring | Lacks documentation for casual users | Free | Free |
| Google Cloud Key Management: Best for a cloud-based option | Provides an external key manager that allows granular control over data | Easy to use | None | $0.06 per month (for keys with protection level software) |
| HashiCorp Vault: Best for secret keys | Open-source and self-hosted; dynamic secrets/just-in-time secrets | Can be complex; takes time to learn | Free with limited features. | Starts at $1.58 per hour |
5 top encryption tools for easing encryption key management
Microsoft Azure Key Vault: Best overall
Microsoft offers a very impressive encryption key management service in the form of Azure Key Vault, with its focus on security and automation.
SEE: 8 Best Identity and Access Management Solutions in 2024 (TechRepublic)
Azure Key Vault allows for importing and generating encryption keys, including those linked to hardware security modules, and to easily monitor and audit their use. These keys stay protected at all times, not even Microsoft itself can access them. As is the focus of a lot of Microsoft’s Azure line, there are plenty of options to simplify and automate Key Vault’s functions, potentially freeing up a lot of time.
Figure A
Why we chose Microsoft Azure Key Vault
We picked Azure Key Vault as our top choice for its high-level balance of security and ease-of-use. It provides an intuitive key management experience, offers automations capabilities and lets managers limit access to sensitive keys. On top of that, it’s designed to reduce key vault latency — which is a must for organizations that are starting to scale and may receive hundreds of requests a day.
Pricing
Azure Key Vault is offered on a pay-as-you-go basis, but Microsoft offers you $200 of credit to use in your first 30 days, and will continue to give you a free monthly allowance on over 55 of their services as long as you’re with them. This means it won’t cost you anything to try this enterprise-level encryption key management system, though long-term costs will vary depending on how much you use each service.
For its Vaults offerings, here’s a brief overview of pricing:
- Secret operations: $0.03/10,000 transactions (Standard).
- Certificate operations: $3 per renewal request, all other operations are at $0.03/10,000 transactions (Standard).
- Managed Azure Storage account key rotation: Free during preview; $1 per renewal.
Features
- Provides easy key management.
- Supports FIPS 140-2 Level 2 hardware security module encryption.
- Automates tasks for TLS/SSL certificates.
- Offers enhanced security and greater control over keys.
- Ensures that apps don’t have access to keys.
Pros
- Designed to reduce latency.
- Easy to use.
Cons
- No free version as with some competing encryption key management solutions.
GnuPG: Best for PGP encryption
GnuPG, or the GNU Privacy Guard, is a free and open-source command line tool that allows for encryption key management as well as easy encryption and signing of data, emails and other communication.
SEE: 6 Best Authenticator Apps for 2024 (TechRepublic)
Although it doesn’t carry as many features as some other key management and encryption packages, it will be more than sufficient for most and more than earns its spot on this list. As a common inclusion on Linux distributions, it’s a very accessible option that is easy to use, provided you can get past the potential intimidation of operating from the command line. Being as widely used as it is and having been around for over 20 years, there are plenty of support options.
As well as easy integration with other common applications, GnuPG also works well with Windows through Gpg4win. This allows for quick and easy setup and additional features such as a context menu tool and a Microsoft Outlook plugin which allows you to easily use your keys for sending and receiving encrypted emails. Thanks to a recent update, GnuPG version two now has S/MIME functionality.
Figure B
Why we chose GnuPG
Gnu Privacy Guard made this list for its open source and free implementation of the OpenPGP standard. As one of the most widely used encryption standards, GnuPG’s OpenPGP service makes it accessible for businesses to encrypt and sign their data. It’s a great option for businesses with technical expertise, especially those who are well-versed in maximizing different integrations that suit their organization’s particular needs.
Pricing
Features
- Provides for auditing, analysis and compliance.
- Has network access control.
- Offers anti-malware, anti-spam and threat detection.
- Supports email encryption.
- Provides access control management and data loss prevention,
- Offers password and identity management.
- Includes firewall, network security and packet analyzers.
- Provides database activity monitoring.
- Offers device control.
- Provides for content filtering.
- Includes endpoint detection and response.
- Includes file encryption.
- Offers end-user awareness and training.
- Includes data recovery.
- Includes digital rights management.
Pro
- Free to use.
- The product has been around for a long time so lots of support options are available.
- There are a number of integrations, so you can use GnuPG on a number of devices and applications.
Cons
- Only supports PGP encryption.
Seahorse: Best for a user-friendly interface
Seahorse is another local encryption key management application that, like GnuPG, is often found on Linux distributions. However, Seahorse offers a larger range of features as well as a graphical user interface, which many will find more comfortable than working with the command line.
SEE: 5 Best Free Password Managers for 2024 (TechRepublic)
As well as allowing you to manage both PGP and SSH encryption keys, Seahorse can manage your other passwords and even allows the use of an image as a photo ID. The interface is easy to use and understand, making adding, removing or updating keys and passwords a quick and easy process, even for those who are not overly technical. The option to back up your keyring is also included, reducing the risk of accidentally losing access to your data.
Integration with other common Linux software including file managers, browsers and email clients combined with passphrase caching makes for a very smooth user experience, though this does mean that you need to take care not to leave your computer unlocked.
Best of all, it is available as a free and open-source product, so there are no upfront costs or subscription fees.
Figure C
Why we chose Seahorse
We selected Seahorse for its user-friendly user interface, which forgoes using the more intimidating command line tool for its implementation. We imagine this simple and beginner-centric encryption key manager to be a good entry-point for users and businesses that want to try out such a service. It’s especially viable for this use-case given that it’s a completely free application.
Pricing
Features
- Allows auto-saving passwords to a keyring.
- Lets users create and manage SSH keys.
- Has limited cross-platform syncing
- Provides password management
- Supports multiple keyrings, each protected by its own master password.
- Allows for generating and managing PGP keys.
- Allows publishing and retrieving encryption keys from key servers.
- Integrates with NetworkManager to store WEP passwords.
- Has a graphical user interface.
Pros
- Features an easy-to-use user interface.
- Manage SSH and PGP keys.
- Good range of features.
Cons
- Passwords in open computerized key cabinets are stored in your physical RAM only.
Google Cloud Key Management: Best for businesses with Google ecosystem
Google has long been one of the biggest names in tech and the Google Cloud Key Management service builds on the company’s history of offering reliable solutions that meet the needs of just about anyone.
SEE: 4 Best Free VPNs for 2024 (TechRepublic)
This is a centralized, cloud-based key management service that can truly take care of everything. It’s able to generate, store, rotate and destroy both symmetric and asymmetric keys for many different encryption systems, including AES256, RSA 4096, and EC P384. Google Cloud also includes the ability to work with external key managers and hardware-based encryption via HSM for ultimate security.
Figure D
Why we chose Google Cloud Key Management
Google’s Cloud Key Management service is great for businesses that are already heavily entrenched in the Google ecosystem. In particular, organizations that are utilizing Google Cloud Platform will feel right at home with Cloud Key Management. On its own, Cloud Key Management offers fast and secure key management. It offers both software and hardware-protected encryption keys and has extensive symmetric and asymmetric key support.
Pricing
Users should be aware that this is a subscription service with a fairly complex pricing system, with the monthly cost being determined by your usage of the various functions it offers.
Here’s a quick glimpse of Google pricing for Cloud Key Management:
- Active symmetric AES-256 and HMAC key versions: $0.06 per month
- Active asymmetric RSA 2048 key versions: $0.06 per month.
- Key operations Cryptographic: $0.03 per 10,000 operations.
These are just a few of Google’s service offerings, with other configurations available depending on your organization’s particular needs and requirements.
Features
- Compatible with encryption hardware.
- Allows creating, managing and deleting encryption keys.
- Provides an external key manager that allows granular control over data.
Pros
- Vast feature set for securing keys.
- Manage both symmetric and asymmetric keys on encryption technologies like AES 256 and RSA-4096.
Cons
- Complicated pricing structure.
HashiCorp Vault: Best for secrets management
HashiCorp Vault is an ideal encryption manager to use for secrets management – secrets being any digital asset an organization wants under tight control. It offers a plethora of features, such as identity-based access and more.
Seamless integration with other software and service providers including Google, Microsoft, and Amazon Web Services is another feature.
Figure E
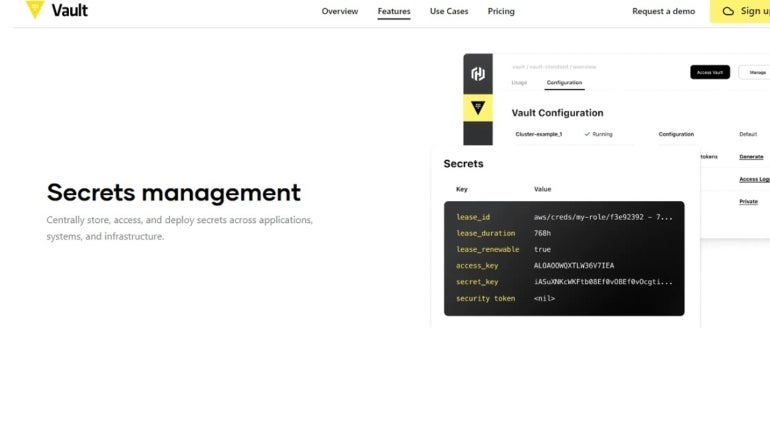
Why we chose HashiCorp Vault
HashiCorp got its service on the list for businesses which specifically require a versatile way to manage secrets and other digital assets. HashiCorp Vault can handle dynamic and static secrets, supports Kubernetes and AWS integration, and includes identity-based security automation. Its dynamic secrets functionality is noteworthy, allowing businesses to generate on demand secrets for just-in-time or one-off use-cases.
Pricing
While HashiCorp Vault is a freemium service, you’ll need to subscribe if you want full access to their identity-based security services, including encryption keys. The exact price you’ll pay varies, with their standard service starting at $1.58 per hour.
Custom setups are also available if you have special security or compliance needs, with more information about what they can offer in this regard available from their sales team.
Features
- Provides secrets management.
- Supports identity-based access.
- Provides data encryption.
- Supports AWS/Kubernetes integration.
Pros
- Easy way to manage secret sprawl.
- Open-source and self-hosted.
- Can generate PKI certificates.
- Fast release cycle.
Cons
- Not so easy to use.
- No readily clear way to search for secret keys.
How to choose encryption key management software
There are a few things to consider when choosing an encryption key management solution:
Security features
Look for a management system that has strong encryption algorithms and safe key storage. Another great feature to look for is key rotation to ensure that your keys are cycled.
Integration
It’s also important to ensure that your key management system will integrate with your existing applications.
Pricing
The truth is that cost plays an important role when vetting key management systems. However, you should never base your decision purely on pricing. Make sure that the option you choose is best suited to your needs. Fortunately, you will find a number of free tools in the list above, but you should always check that the software solution offers the kind of functionality you’re looking for.
Physical vs. cloud-based storage
When choosing software to manage cryptographic keys, you will also need to think about cloud-based versus. physical storage. This is primarily a preference-based choice, as some find peace of mind in choosing a local storage solution as opposed to a cloud-based one. Still, cloud-based systems can also provide greater accessibility, so it’s something worth considering.
Frequently asked questions
What Is encryption key management software?
Encryption key software is a system that creates, manages, and uses cryptographic keys to encrypt and decrypt sensitive data. These keys are critical for protecting online data. The software ensures that encrypted data is unreadable by unauthorized users, protecting it from potential cyber-attacks.
It also ensures the safe key storage, distribution, and rotation of keys, which is critical for ensuring the integrity and confidentiality of information across several applications and systems.
What are the key features of encryption key management software?
Here are some of the most important features to look for when choosing the right software solution to manage encryption keys:
- Integration
- Generation of symmetric and asymmetric keys
- Threat protection
- Access control
- Key recovery
- Secure key control and storage
- Hardware security modules
What are the benefits of encryption key management software?
Encryption key management software and cloud-based services can help to ensure confidentiality so that only authorized persons can gain access to sensitive information. It also maintains the integrity of data, as it prevents tampering and makes data accessible through the use of encryption keys.
Cryptographic operations also help to maintain online security by preventing data breaches and cyber-attacks.
What is key management in encryption?
Encryption key management is the term used to describe the administration of the methods and policies used to organize, safeguard, store and distribute keys.
What are the three types of encryption keys?
The three types of encryption keys are as follows:
- Symmetric encryption keys. These keys are used in symmetric encryption, which employs the usage of the same key for both encryption and decryption. It is a quick and effective solution, but it requires safe key delivery.
- Asymmetric keys. Asymmetric encryption uses two keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, whereas the private key has to be kept hidden, resulting in a more secure key exchange method.
- Hashing. Hashing generates a fixed-size number from data using a one-way function to ensure that it remains authentic and integral. While not used for encryption, these keys are essential for message authentication and digital signatures.
What are the most secure encryption techniques?
The most secure techniques for encryption include:
- RSA (Rivest-Shamir-Adleman). An asymmetric encryption technique that is commonly used for the safe exchange of keys and electronic signatures. This method relies on the mathematical features of prime numbers.
- ECC (Elliptic Curve Cryptography). This is also an asymmetric encryption technique that offers comparable safety with lower key lengths, which makes it more efficient in cases where there are limited resources.
- AES (Advanced Encryption Standard). This method uses symmetric encryption key lengths of 256, 128, or 192 bits that have become the standard in the industry for safeguarding private information with encryption, thanks to its speed and reliability.
- SHA-3 (Secure Hash Algorithm 3). Unlike the other three, SHA-3 is a hash function employed for digital signatures along with data verification to prevent collision attacks and ensure the integrity of the data.
Methodology
Like all security products we evaluate, we examined the best encryption key management software for their value in terms of additional security and overall value.
For this product category we looked at each provider’s symmetric and asymmetric key offerings, access control and security key and control, threat protection, hardware security modules and key recovery, among others. We also took into account ease of implementation and how easy it is to use each software.
Research for the above consisted of extensive evaluation of each vendor’s official documentation, feature inclusions, pricing and verified user feedback and testimonials.
Finally, we took into consideration how each software provider could benefit a particular use-case or business use. This allows us to make the best encryption key management recommendations to organizations with specific needs and requirements.
Using SSH and encrypting your data are the biggest steps organizations can take to ensure that all their private information remains safe and secure and away from prying eyes. However, there are challenges with managing encryption. First, losing encryption keys means losing access to data. Second, if a malicious actor gets hold of an organization’s…
Using SSH and encrypting your data are the biggest steps organizations can take to ensure that all their private information remains safe and secure and away from prying eyes. However, there are challenges with managing encryption. First, losing encryption keys means losing access to data. Second, if a malicious actor gets hold of an organization’s…
